Beyond compliance
A comprehensive privacy management program provides an effective way to satisfy regulators and assure compliance. But it is more than that. Done right, such a program helps foster a culture of privacy that builds trust, and increases operational efficiency, including bottom-line results. Senior management support is vital in achieving business benefits when working on privacy compliance. When senior management provides the needed resources to ensure appropriate training and education, it sends a clear signal that privacy is vital to the organization.
Organizations that treat privacy as vital to their operations, by implementing a robust privacy management program, benefit from greater trust and engagement from customers and clients. They also enjoy an enhanced reputation that can give them a competitive edge. In the longer term, a privacy management program that is scaled to the organization’s needs will save money and make good business sense.
Compliance fundamentals
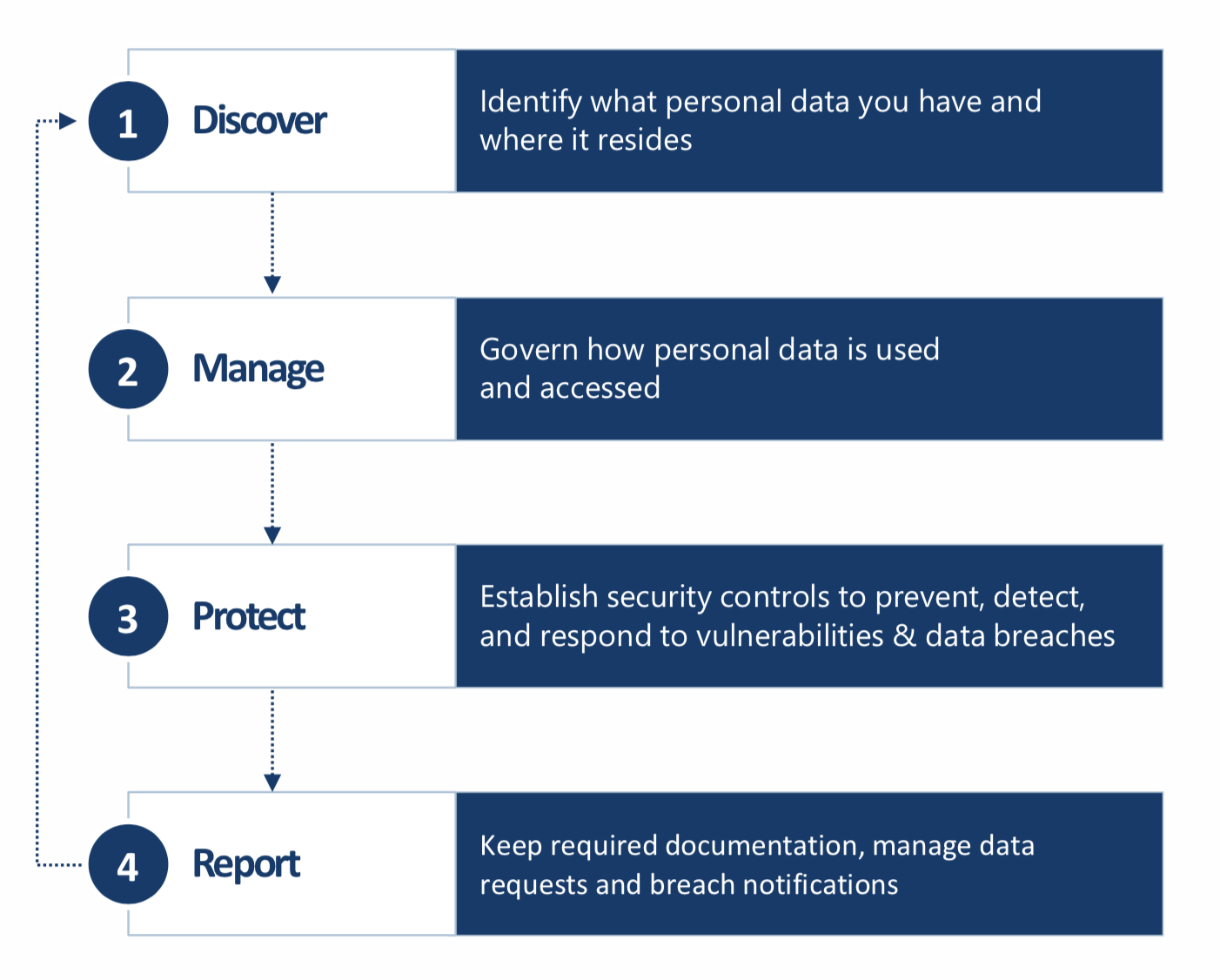
What should an organization do to ensure that it is handling personal information appropriately? How will it know that it is doing it right? How will it be able to demonstrate to its clients, partners and to the authorities that it has the capacity to comply with its legal obligations? An organization that processes personal data is required to implement and maintain a privacy protection program. It needs to define policies and processes, as well as provide role-specific employee privacy training. It needs to have contracts in place if it transfers personal information to other companies for processing, to ensure that the information in question is adequately protected. Organizations are expected to have a an easy-to-understand public privacy policy in place, with clear procedures to respond to requests from individuals for access to (and correction of) their personal information. It needs to be able to respond to complaints from individuals about how personal information is being used and protected, with regularly maintained documentation.
Achieving compliance
Building trust
Identifying where your organization can gain a competitive advantage while complying with local and international privacy laws should be one of your top priorities if you want to thrive in an increasingly data-driven environment. Boosting operational efficiency, increasing sales, and fostering trust, can all be gained by developing a tailored privacy management program. Identifying and purging sensitive, redundant, obsolete and trivial data of no business value lowers operational costs. Lean, fine-tuned databases of highly relevant data increase productivity and efficiency. Role-specific privacy training to relevant employee groups can increase growth and business opportunities. Ensuring personal data is safe will increase customer trust and enable your organization to use that data to offer services customers want.
To hear how we can help you build a privacy management program that benefits all areas of your organization, get in touch. Contact us